If you’ve ever seen 264.68.111.161, you might think it’s just another IP address, but it actually raises interesting questions about how networks work. This number follows the familiar dotted-decimal pattern, with each octet representing part of a network address, yet it falls outside the standard numerical range. Understanding why this matters can improve your grasp of device communication and network configuration.
Even in everyday technology, concepts like firewalls, cybersecurity, and data packets rely on proper IP formats. By exploring addresses, you’ll see how technical rules keep systems secure and ensure smooth connectivity in modern digital life.
What is 264.68.111.161?
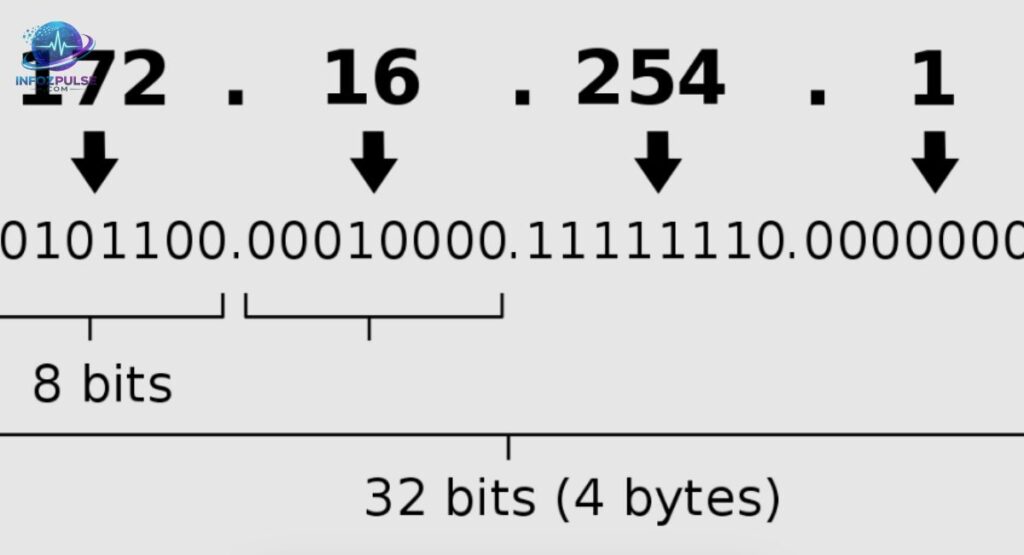
Appears as a standard IPv4 address, following the familiar dotted-decimal pattern of four numerical segments. Each segment, or octet, typically ranges from 0 to 255. This structure helps devices communicate efficiently, but 264.68.111,161 actually falls outside valid ranges, making it an interesting case for both beginners and professionals.
People often assume any dotted sequence is valid, but understanding network standards shows that technical validation is essential. Learning about addresses like this helps you grasp system administration and the rules behind digital communication.
How 264.68.111.161 Works
The address follows a visual pattern similar to regular IP addresses, but its first octet exceeds the standard numerical range. This means it cannot be assigned to a device or used in standard routing traffic. Recognizing such patterns helps you avoid errors in network infrastructure management.
For tech professionals, encountering invalid addresses is common during software testing or reviewing logs. They serve as examples to refine validation rules and prevent configuration issues, making your networks more secure and reliable.
Key Benefits
Studying 264.68.111.161 offers practical benefits. It helps you understand technical limitations in networking, which can prevent mistakes in cybersecurity and access control lists. Knowing why certain addresses fail ensures devices communicate correctly without disruption.
Additionally, learning about IP structures improves your awareness of digital identity and network configuration. It equips you to plan security measures better and maintain healthy network connections across your devices.
Practical Uses
Even though 264.68.111,161 is invalid, it has practical applications in testing and education. Developers often use it in log generation or error handling to simulate misconfigured networks without risking real systems.
System administrators also encounter similar patterns when monitoring data packets or verifying network rules. Studying these examples improves your skills in cloud services and maintaining robust device communication.
Differences from Traditional Methods

Unlike valid IPv4 addresses, 264.68.111,161 highlights the importance of correct network address allocation. Traditional IPs adhere to strict binary value calculations, ensuring proper routing and connectivity, whereas this address violates those standards.
Comparing it to modern methods, like IPv6 with hexadecimal values, shows how networks have evolved to prevent errors and address exhaustion. Understanding these differences improves your digital literacy and technical awareness.
Challenges or Limitations
One major limitation of addresses like 264.68.111.161 is their inability to function in real networks. Devices cannot recognize them, and firewalls or intrusion detection systems may flag them as malformed.
Such addresses can confuse beginners who rely on visual patterns. Misinterpreting them may lead to misconfigured network tools or failed system administration tasks, highlighting the need for proper training and guidance.
Implementation Tips
If you are testing networks or applications, use 264.68.111.161-type values safely in software testing or educational environments. They help you understand technical rules without impacting real systems.
Always pair testing with valid private IP ranges and standard network standards. This ensures your experiments demonstrate the correct routing traffic principles and teach safe digital identity management.
Tools & Platforms
Several tools can help analyze addresses, such as network monitoring software and log analyzers, which provide insights into data packet handling and potential configuration errors.
Platforms for cloud hosting or network infrastructure management can simulate invalid addresses to improve error handling and validation rules. Using these tools ensures your networks remain secure and properly configured.
Future Trends
As networks evolve, IP address structures will continue to change. IPv6 adoption reduces reliance on IPv4, addressing limitations like address exhaustion and increasing connectivity options.
Understanding examples like 264.161 prepares you for future challenges in cybersecurity, cloud computing, and system administration. Knowledge of invalid addresses enhances your ability to plan and maintain resilient networks.
Conclusion
264.68.111.161 may look like a normal IP, but studying it teaches critical lessons in network standards, technical limitations, and safe digital practices. By exploring invalid addresses, you strengthen your digital literacy, improve device communication, and learn how to protect networks against errors. Whether you manage systems professionally or study networking, understanding these concepts is essential for modern tech environments.
Meta Description
264.68.111.161 looks like an IP address, but is it valid? Learn what it means, how IP rules work, and why accuracy matters in networking.

Welcome to Infoz Pulse! I am dedicated to helping businesses improve their online presence and achieve growth through effective SEO strategies.
